GandCrab v4.1 in the wild — first Windows XP and Server 2003 impacting ransomware SMB worm

GandGrab 4 landed this month. There’s a couple of notable things — it no longer needs a C2 server (it can operate in airgapped environments, for example) and it now spreads via an SMB exploit — including on XP and Windows Server 2003 (along with modern operating systems). As far as I’m aware, this is the first ransomware true worm which spreads to XP and 2003 — you may remember much press coverage and speculation about WannaCry and XP, but the reality was the NSA SMB exploit (EternalBlue.exe) never worked against XP targets out of the box.
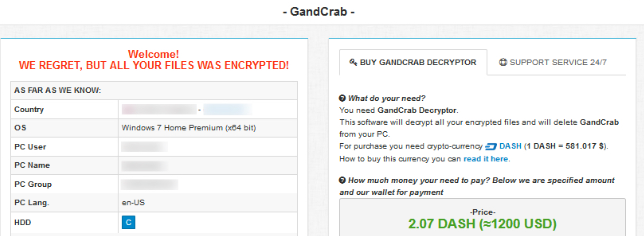
For those who haven’t been following GandGrab, it’s a ransomware operation where people pay for the kit, and earn money by spreading it. Notably it usually only impacts organisations and people with poor security and/or security practice — e.g. people tend to embed it into keygens on BitTorrent, that sort of thing. Most antivirus software can detect it quickly.
However being able to spread without internet access and impacting legacy XP and 2003 systems suggests some older environments may end up at risk where there is poor security practice — e.g. no working antivirus software.
The version 4 strain uses the file extension .KRAB. Network spreading still has this deliciously named module:

Aside from using UNC accessible network shares to spread, it also now appears to hunt unpatched Windows systems.
Mitigations
Install patch MS17–010.
This patch is available for all operating systems — including back to Windows XP and Windows Server 2003 — since early 2017. There is no patch for Windows 2000.
Keep up to date antivirus software, including in legacy environments.
Many antivirus products have dropped support for Windows XP and 2003, which makes this problematic.
Policies
You probably want to make sure staff know not to download things from BitTorrent, install unknown software, run keygens, access random USB sticks etc.
Network zoning
If you have legacy equipment, you may want to restrict inbound access. Also you may want to keep business units separate, so an incident in one area doesn’t spread (see also: NHS and WannaCry).
Stop using SMB1
You can find out more from the guy who manages SMB at Microsoft here. This isn’t an option for XP and 2003 systems, however for later systems which don’t talk back to legacy kit, you can safely test and disable SMB1 — centrally through Group Policy, too — it’s just a registry key.
Server 2012 R2 and Server 2016
- Server Manager: Disable SMB 1.0/CIFS File Sharing Support (Feature)
- PowerShell: Remove-WindowsFeature FS-SMB1
Windows Client (8.1 and 10)
- Remove the Windows Feature SMB 1.0/CIFS File Sharing Support
- PowerShell: Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
Windows Vista/7/2008/2008 R2
- You can use the registry and set this value to 0: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters\SMBv1 (1 is enabled)
IOCs
8ecbfe6f52ae98b5c9e406459804c4ba7f110e71716ebf05015a3a99c995baa1
SMB1 traffic (you can spot this on the wire, or by enabling SMB1 monitoring in the registry and looking at the Event Log in Windows)
lsass.exe process writing out to temp folder — you can monitor lsass.exe through Microsoft Sysmon, if it starts writing out and executing new files, you’re going to have a bad day.

